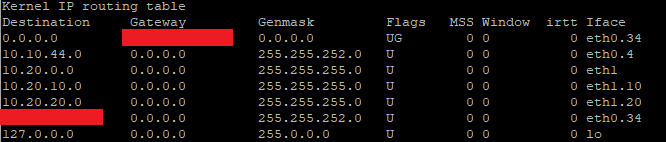
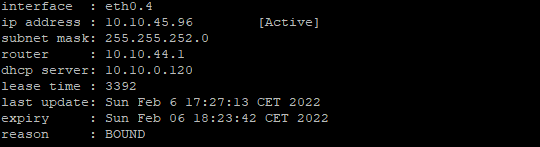
Ik heb commando ‘mca-ctrl -t dump-cfg > config.gateway.json-compleet’ uitgevoerd (via PuTTY). Dit levert de volgende output op (deel 1):
{
"firewall": {
"all-ping": "enable",
"broadcast-ping": "disable",
"group": {
"address-group": {
"authorized_guests": {
"description": "authorized guests MAC addresses"
},
"guest_allow_dns_servers": {
"description": "allow dns servers for guests"
},
"guest_portal_address": {
"description": "guest portal address"
},
"guest_pre_allow": {
"description": "allow addresses for guests"
},
"guest_restricted": {
"address": [
"192.168.0.0/16",
"10.0.0.0/8",
"172.16.0.0/12"
],
"description": "restricted addresses for guests"
},
"unifi_controller_addresses": {
"description": "UniFi addresses"
}
},
"ipv6-network-group": {
"corporate_networkv6": {
"description": "IPv6 corporate subnets"
},
"guest_networkv6": {
"description": "IPv6 guest subnets"
}
},
"network-group": {
"captive_portal_subnets": {
"description": "captive portal subnets"
},
"corporate_network": {
"description": "corporate subnets",
"network": [
"10.20.10.0/24",
"10.20.0.0/24"
]
},
"guest_network": {
"description": "guest subnets",
"network": [
"10.20.20.0/24"
]
},
"remote_client_vpn_network": {
"description": "remote client VPN subnets"
},
"remote_site_vpn_network": {
"description": "remote site VPN subnets"
},
"remote_user_vpn_network": {
"description": "Remote User VPN subnets"
}
},
"port-group": {
"guest_portal_ports": {
"description": "guest portal ports"
},
"guest_portal_redirector_ports": {
"description": "guest portal redirector ports",
"port": [
"39080",
"39443"
]
},
"unifi_controller_ports-tcp": {
"description": "unifi tcp ports",
"port": [
"8080"
]
},
"unifi_controller_ports-udp": {
"description": "unifi udp ports",
"port": [
"3478"
]
}
}
},
"ip-src-route": "disable",
"ipv6-name": {
"AUTHORIZED_GUESTSv6": {
"default-action": "drop",
"description": "authorization check packets from guest network"
},
"GUESTv6_IN": {
"default-action": "accept",
"description": "packets from guest network",
"rule": {
"3001": {
"action": "drop",
"description": "drop packets to intranet",
"destination": {
"group": {
"ipv6-network-group": "corporate_networkv6"
}
}
}
}
},
"GUESTv6_LOCAL": {
"default-action": "drop",
"description": "packets from guest network to gateway",
"rule": {
"3001": {
"action": "accept",
"description": "allow DNS",
"destination": {
"port": "53"
},
"protocol": "udp"
},
"3002": {
"action": "accept",
"description": "allow ICMP",
"protocol": "icmp"
}
}
},
"GUESTv6_OUT": {
"default-action": "accept",
"description": "packets forward to guest network"
},
"LANv6_IN": {
"default-action": "accept",
"description": "packets from intranet"
},
"LANv6_LOCAL": {
"default-action": "accept",
"description": "packets from intranet to gateway"
},
"LANv6_OUT": {
"default-action": "accept",
"description": "packets forward to intranet"
},
"WANv6_IN": {
"default-action": "drop",
"description": "packets from internet to intranet",
"rule": {
"3001": {
"action": "accept",
"description": "allow established/related sessions",
"state": {
"established": "enable",
"invalid": "disable",
"new": "disable",
"related": "enable"
}
},
"3002": {
"action": "drop",
"description": "drop invalid state",
"state": {
"established": "disable",
"invalid": "enable",
"new": "disable",
"related": "disable"
}
}
}
},
"WANv6_LOCAL": {
"default-action": "drop",
"description": "packets from internet to gateway",
"rule": {
"3001": {
"action": "accept",
"description": "Allow neighbor advertisements",
"icmpv6": {
"type": "neighbor-advertisement"
},
"protocol": "ipv6-icmp"
},
"3002": {
"action": "accept",
"description": "Allow neighbor solicitation",
"icmpv6": {
"type": "neighbor-solicitation"
},
"protocol": "ipv6-icmp"
},
"3003": {
"action": "accept",
"description": "allow established/related sessions",
"state": {
"established": "enable",
"invalid": "disable",
"new": "disable",
"related": "enable"
}
},
"3004": {
"action": "drop",
"description": "drop invalid state",
"state": {
"established": "disable",
"invalid": "enable",
"new": "disable",
"related": "disable"
}
}
}
},
"WANv6_OUT": {
"default-action": "accept",
"description": "packets to internet"
}
},
"ipv6-receive-redirects": "disable",
"ipv6-src-route": "disable",
"log-martians": "enable",
"name": {
"AUTHORIZED_GUESTS": {
"default-action": "drop",
"description": "authorization check packets from guest network"
},
"GUEST_IN": {
"default-action": "accept",
"description": "packets from guest network",
"rule": {
"3001": {
"action": "accept",
"description": "allow DNS packets to external name servers",
"destination": {
"port": "53"
},
"protocol": "tcp_udp"
},
"3002": {
"action": "accept",
"description": "allow packets to captive portal",
"destination": {
"group": {
"network-group": "captive_portal_subnets"
},
"port": "443"
},
"protocol": "tcp"
},
"3003": {
"action": "accept",
"description": "allow packets to allow subnets",
"destination": {
"group": {
"address-group": "guest_pre_allow"
}
}
},
"3004": {
"action": "drop",
"description": "drop packets to restricted subnets",
"destination": {
"group": {
"address-group": "guest_restricted"
}
}
},
"3005": {
"action": "drop",
"description": "drop packets to intranet",
"destination": {
"group": {
"network-group": "corporate_network"
}
}
},
"3006": {
"action": "drop",
"description": "drop packets to remote user",
"destination": {
"group": {
"network-group": "remote_user_vpn_network"
}
}
},
"3007": {
"action": "drop",
"description": "allow authorized and drop unauthorized",
"destination": {
"group": {
"address-group": "authorized_guests"
}
}
},
"6001": {
"action": "accept",
"description": "accounting defined network 10.20.20.0/24",
"source": {
"address": "10.20.20.0/24"
}
}
}
},
"GUEST_LOCAL": {
"default-action": "drop",
"description": "packets from guest network to gateway",
"rule": {
"3001": {
"action": "accept",
"description": "allow DNS",
"destination": {
"port": "53"
},
"protocol": "tcp_udp"
},
"3002": {
"action": "accept",
"description": "allow ICMP",
"protocol": "icmp"
},
"3003": {
"action": "accept",
"description": "allow to DHCP server",
"destination": {
"port": "67"
},
"protocol": "udp",
"source": {
"port": "68"
}
}
}
},
"GUEST_OUT": {
"default-action": "accept",
"description": "packets forward to guest network",
"rule": {
"6001": {
"action": "accept",
"description": "accounting defined network 10.20.20.0/24",
"destination": {
"address": "10.20.20.0/24"
}
}
}
},
"LAN_IN": {
"default-action": "accept",
"description": "packets from intranet",
"rule": {
"6001": {
"action": "accept",
"description": "accounting defined network 10.20.10.0/24",
"source": {
"address": "10.20.10.0/24"
}
},
"6002": {
"action": "accept",
"description": "accounting defined network 10.20.0.0/24",
"source": {
"address": "10.20.0.0/24"
}
}
}
},
"LAN_LOCAL": {
"default-action": "accept",
"description": "packets from intranet to gateway"
},
"LAN_OUT": {
"default-action": "accept",
"description": "packets forward to intranet",
"rule": {
"6001": {
"action": "accept",
"description": "accounting defined network 10.20.10.0/24",
"destination": {
"address": "10.20.10.0/24"
}
},
"6002": {
"action": "accept",
"description": "accounting defined network 10.20.0.0/24",
"destination": {
"address": "10.20.0.0/24"
}
}
}
},